Tonga Cybersecurity Manual
Purpose:
The purpose of the Tonga Cybersecurity Manual is to provide strategic
and practical guidance on how organizations in Tonga can protect their systems
and data from cyber threats.
Scope:
The manual was developed
taking into account internationally recognized IT security frameworks,
especially ISO standards ISO/IEC 27002 (Code of practice for information
security controls) and ISO/IEC 27005 (Information security risk management).
Target audience:
The Tonga
Cybersecurity Manual is targeted at Tongan Government agencies to
improve the overall security profile and ICT capabilities across the government.
The manual also addresses enterprises through raising risk awareness and improving
corporate cyber hygiene.
Steps of Cybersecurity Management
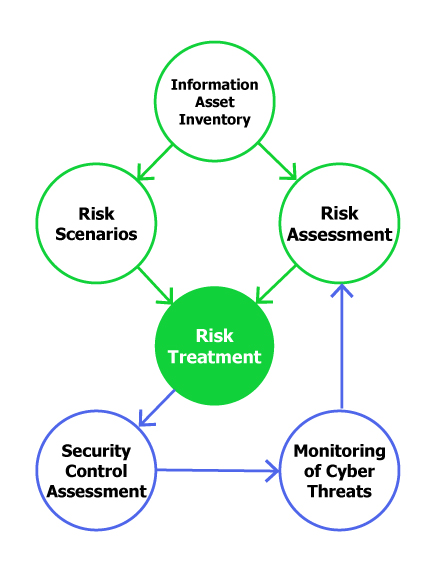
Figure 1: Steps of cybersecurity management
The
Management of the organization initiates the implementation of the Tonga
Cybersecurity Manual by assigning a responsible person for the information
security management (see also 1.1.2 Information security roles and responsibilities).
Furthermore, the Management is responsible for providing the required
resources, e.g. training, time and finances. For efficient and effective
implementation, the Management should support the information security manager
with high-level decisions and receive and review periodical overviews about the
progress of information security management and information security incidents.
There
are several vital steps to be performed in the process of cybersecurity
implementation. These steps are cyclical (the completion of the last step
initiates the first step one more time, ideally within annual cycles) and are
descibed in detail in the next chapters. They can be summarized as follows:
1.
INFORMATION
ASSET INVENTORY
Protection
of information assets starts with establishing a clear picture of the organization’s
information assets – systems, applications, data and other resources that are
vital to keeping information systems running. Secondly, system owners assign
systems and data with the requirements of confidentiality, integrity and
availability.
2.a.
[BASELINE]
RISK SCENARIOS
Once
the organization has a good understanding of what systems and data need
protection, security risks are identified, analysed and evaluated. For smaller
organizations, a simplified method of risk scenarios can be used as a step in
cyber risk management.
2.b.
[ADVANCED]
RISK ASSESSMENT
Risk
assessment identifies the applicable threats and vulnerabilities, determines
the potential consequences and, finally, prioritizes the derived risks.
3.
RISK
TREATMENT
All
important cyber security risks that can impact systems and data are managed by
selecting and applying protective measures – the security controls. The highest
risks should be considered with highest priority.
4.
SECURITY
CONTROL ASSESSMENT
After
the security controls have been applied, an assessment of their effectiveness
must be introduced in order to verify that the measures are implemented
correctly and are operating as intended.
5.
MONITORING
OF CYBER THREATS
Finally,
as the cyber security environment never stops changing, monitoring of cyber
threats and associated risks must be introduced to enable corrective actions.