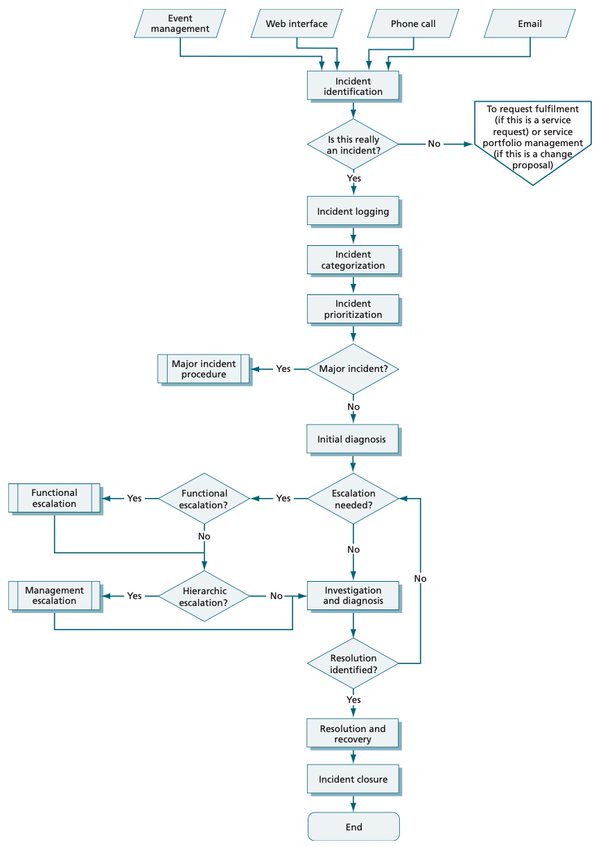
11.1.1 Responsibilities and
procedures
Management responsibilities and procedures should be established to ensure a quick, effective and orderly response to information security incidents.
The objectives for information
security incident management should be agreed with management, and it should be
ensured that those responsible for information security incident management
understand the organization’s priorities for handling information security
incidents.
1) Develop and and communicated
adequately within the organization procedures for:
- incident response planning and preparation,
including procedures for escalation, controlled recovery from an incident and
communication to internal and external people or organizations;
- monitoring, detecting, analysing
and reporting of information security events/weaknesses and incidents;
- logging incident management
activities.
2) Procedures, including management
responsibilities, ensure that:
- competent personnel handle the
issues related to information security events and incidents;
- people are aware of a point of
contact for security incidents’ detection and reporting;
- appropriate contacts with
authorities to handle the information security incidents are maintained.
3) Reporting procedure:
- includes reporting forms ie templates
that support the reporting action and help the person reporting to describe all
necessary actions in case of an information security event;
- describes all necessary
activities e.g. noting all details immediately, such as type of non-compliance
or breach, occurring malfunction, messages on the screen and reporting to the
point of contact;
- references to formal disciplinary
process for dealing with employees who commit security breaches;
- describes suitable feedback
processes to ensure that those persons reporting information security events
are notified of results after the issue has been dealt with and closed.
11.1.2 Reporting information
security events and weaknesses
Information security events should be reported through appropriate management channels as quickly as possible.
- Make sure that all employees and
contractors are aware of their responsibility to report information security
events as quickly as possible and the point of contact to which the events
should be reported.
- Situations to be considered
reporting include:
a) breach of information integrity, confidentiality or availability
expectations;
b) malfunctions of software or hardware as they may be an indicator of a
security attack;
c) any observed
or suspected information security weakness in systems or services;
d) human errors;
e) access violations
f) non-compliances with policies or guidelines
g) breaches of physical security arrangements;
h) uncontrolled system changes;
i) ineffective security control.
11.1.3 Assessment of information
security events
Information security events should be assessed and it should be decided if they are to be classified as information security incidents.
- Create agreed classification
scale that helps to identify the impact and extent of an incident and thereby
prioritize them. The point of contact records and assesses each information
security event using the scale and decides whether the event should be
classified as an information security incident.
- If the organization
has a person responsible for information security, the assessment and decision
can be forwarded to this person for confirmation or reassessment
Read more: 6. Taxonomy
Classification in the Common Taxonomy for Law
Enforcement and The National Network of CSIRTs, https://www.europol.europa.eu/cms/sites/default/files/documents/common_taxonomy_for_law_enforcement_and_csirts_v1.3.pdf
11.1.4 Response to information
security incidents
Information security incidents should be responded to in accordance with the procedures.
- Nominate a point of contact and
other relevant persons inside or outside the organization that respond to
information security incidents.
- To respond to incident and initiate
the necessary recovery:
a) collect
evidence as soon as possible;
b) conduct
forensics analysis if applicable;
c) escalate, if
required;
d) ensure that
all response activities are logged for later analysis;
e) communicate
the existence of the incident to other internal and external people with a
need-to-know;
f) deal with
information security weakness(es) found to cause the incident;
g) close and record
the incident after solving the incident. If necessary, analyse the incident
additionally to identify the source of the incident.
11.1.5 Learning from information
security incidents
Knowledge gained from analysing and resolving information security incidents should be used to reduce the likelihood or impact of future incidents.
- Analyse and evaluate continuously
the reports of information security incidents by type, volume and cost to
identify recurring or high impact incidents.
- Introduce enhanced or additional
controls or review the internal procedures to limit the frequency, damage and
cost of future incidents.
- Include the
information of high impact incidents into the user awareness training and
explain how to respond to such incidents and how to avoid them in the future.
11.1.6 Collection of evidence
The organization should define and apply procedures for the identification, collection, acquisition and preservation of information, which can serve as evidence.
- For the purposes of disciplinary
and legal action, develop and follow internal procedures when dealing with
evidence. When collecting evidence, the chain of custody principle should be
followed. Chain of custody is a process that tracks the movement of evidence
through its collection, safeguarding, and analysis life cycle by documenting
each person who handled the evidence, the date and time it was collected or
transferred, and the purpose for the transfer.
- When an information security
event is detected, it may not be obvious whether or not the event will result
in court action. Therefore, the danger exists that necessary evidence is
destroyed intentionally or accidentally before the seriousness of the incident
is realized. It is advisable to involve police or CERT Tonga early in any
action.
- In case forensic evidence
transcends organizational or jurisdictional boundaries, contact CERT Tonga and
ensure that the organization or person is entitled to collect the required
information as forensic evidence and the internationally acknoledged
requirements are followed.

Figure 5: Forensic process according to NIST Special Publication 800-86.
Read more: