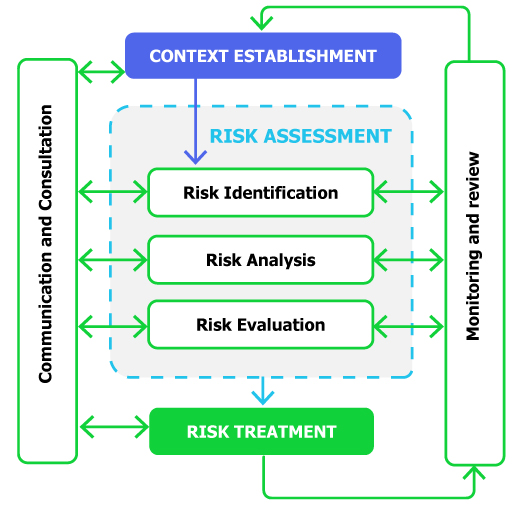
Risk identification
The purpose of risk
identification is to determine what can happen to cause a potential loss, and
to gain insight into how, where and why the loss can happen. Risk
identification requires input from identification of threats, existing
controls, vulnerabilities and consequences.
Identification of threats
A threat has the
potential to harm assets such as information, processes and systems and,
therefore, organizations. Threats can be of natural or human origin, and can be
accidental or deliberate. Both accidental and deliberate threat sources should
be identified. A threat can arise from within or from outside the organization.
Input to the threat
identification can be obtained from the asset owners or users, human resources
staff, facility management and information security specialists, physical
security experts, legal department, the CERT, and other relevant organizations.
Internal experience from incidents and past threat assessments should be
considered in the current assessment.
Identification of existing controls
Identification of
existing controls should be made to avoid unnecessary work or cost, e.g. in the
duplication of controls. In addition, while identifying the existing controls,
a check should be made to ensure that the controls are working correctly.
An existing control can
be identified as ineffective, or insufficient, or not justified. If not
justified or insufficient, the control should be checked to determine whether
it should be removed, replaced by another more suitable control, or whether it
should stay in place, for example, for cost reasons.
Identification of vulnerabilities
Vulnerabilities can be
identified in the areas of organization, processes, management routines,
personnel, environment, system configuration or equipment. The presence of a
vulnerability does not cause harm in itself, as there needs to be a threat
exploiting it. A vulnerability that has no corresponding threat may not require
the implementation of a control, but should be recognized and monitored for
changes.
Identification of consequences
A consequence can be
loss of effectiveness, adverse operating conditions, loss of business,
reputation, or damage. This activity identifies the damage or consequences to
the organization that can be caused by an incident scenario. An incident
scenario is the description of a threat exploiting a certain vulnerability or
set of vulnerabilities in an information security incident.