Risk Treatment and Security Controls
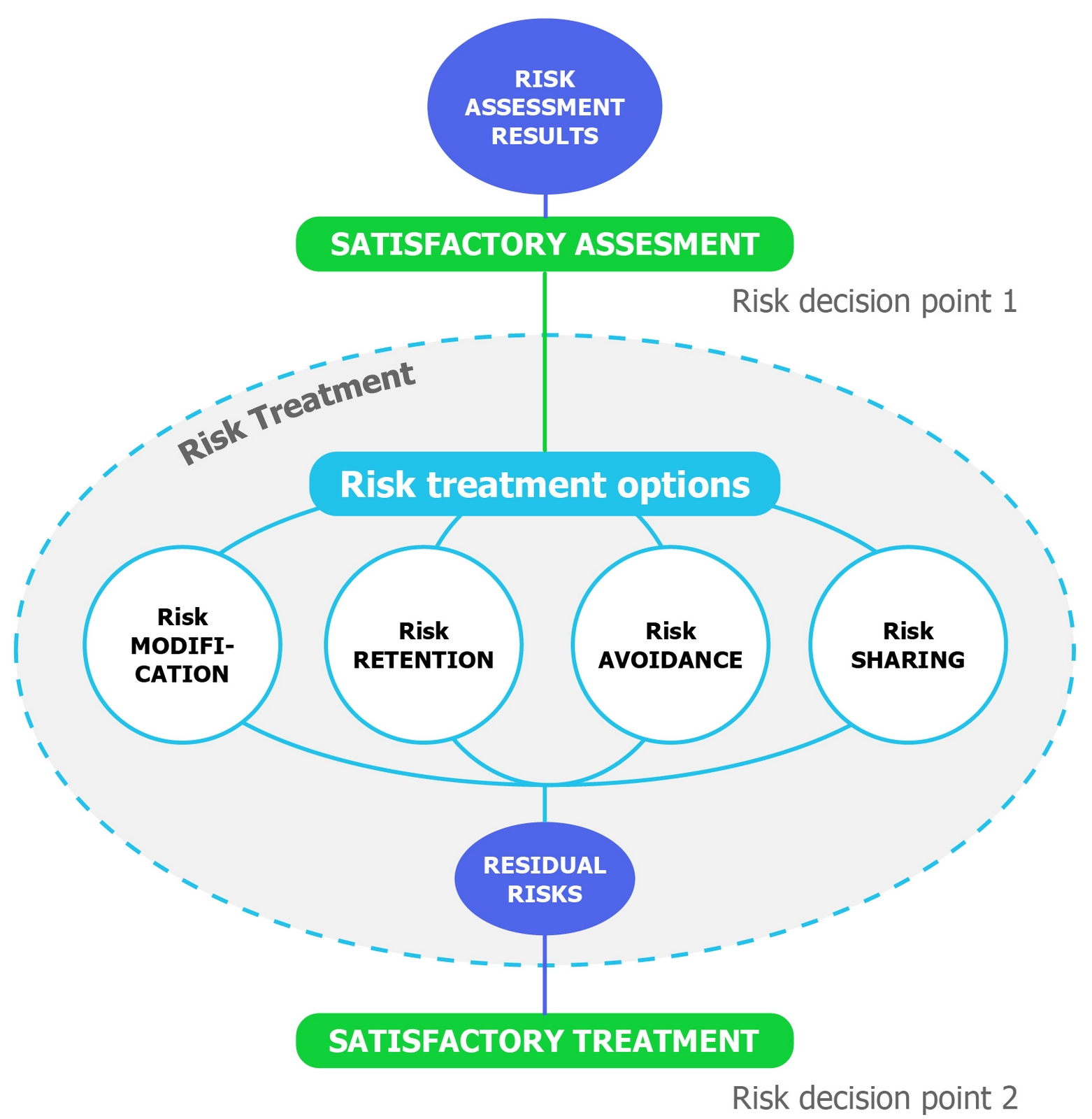
Figure 3. Risk treatment activity according to ISO/IEC 27005:2018

Figure 3. Risk treatment activity according to ISO/IEC 27005:2018
In general, risk treatment gives four options to consider for each and every identified risk. These options are risk modification, retention, avoidance and risk sharing.
Specific risk treatment
starts with selecting the appropriate treatment option – risk modification,
retention, avoidance or sharing. According to the chosen risk treatment option,
security controls for the system can now be selected and tailored to achieve the
desired security objectives. Once the applicable security controls have been
identified for a system, the implementation process follows. To facilitate the
risk treatment process, a tool (see Annex 1) has been created that helps to record details about the
implementation status of the control, required resources, responsible persons
and deadlines of control implementation.
The following listed
security controls should be considered as a baseline, and not be considered as an
exhaustive list of applicable security controls.
The security controls
listed in this manual cover the following domains:
created with
Website Builder Software .